🔍 Section 1: Understanding the RDP Login Error
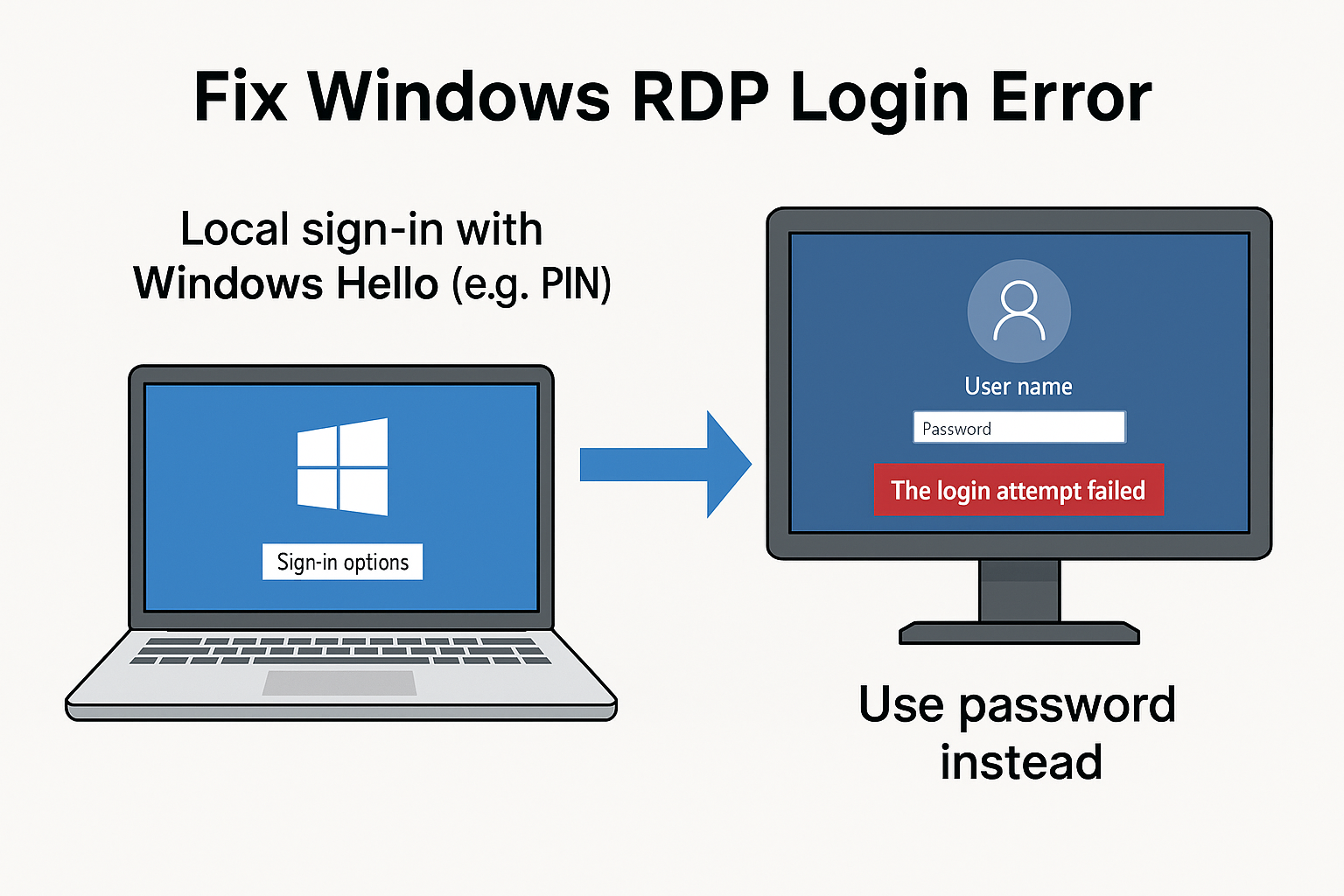
Fix Windows RDP Login Error by understanding a subtle yet critical limitation in how Windows handles authentication. Remote Desktop Protocol (RDP) is a built-in feature in Windows that allows users to access their PCs remotely—whether for system administration, remote technical support, or simply working from another location. It gives users the ability to interact with their machines as if they were physically present.
However, despite entering the correct credentials, many users encounter a frustrating and often misunderstood problem: the RDP login fails without any clear explanation. This issue can be especially puzzling because the system appears fully operational, the network is accessible, and the account being used has the appropriate permissions. In reality, the root cause often lies in the method used to sign in locally—specifically, the use of Windows Hello instead of a traditional password.
This error is particularly frustrating because it typically occurs under seemingly normal conditions. You try to connect to your Windows 10 or Windows 11 machine from another computer using Remote Desktop. You input the username and password you know are correct. And yet, you are met with one of several unhelpful and ambiguous error messages, such as:
- “The login attempt failed.”
- “Your credentials did not work.”
- “Access is denied.”
At first glance, this seems like a simple case of a wrong password or a mistyped username. Naturally, users double-check their input, reset passwords, or even attempt to recreate user accounts. But the login continues to fail—and it becomes clear that something deeper is going on.
🤔 A Misleading User Experience
One of the most challenging aspects of this problem is how deceptive it is. You’re not actually entering the wrong credentials. In fact, the system may even recognize your account, display your profile picture, and give you the illusion that you’re almost in. But the actual handshake between the RDP client and the Windows authentication system fails silently in the background.
This isn’t a network issue. Your IP address is correct. The firewall is open. The user account exists and is authorized for remote desktop use. But for some reason, Windows just won’t let you in remotely.
🧩 The Clue You Didn’t Know to Look For
The real clue lies in how you logged into the PC locally before attempting remote access. If you used a Windows Hello method—such as a PIN code, facial recognition, or fingerprint—to log in, then your system may never have actually used or validated your real password in the current session.
Since RDP requires password-based authentication, this absence of a password in the session context leads to an authentication failure—even if the user technically has the right credentials.
This subtle nuance is almost never explained to users. Microsoft’s error messages don’t reference Windows Hello. The Remote Desktop client doesn’t give specific guidance. As a result, users are left chasing ghost errors, unaware that the root cause lies in a feature designed to improve security and convenience.
Table of Contents
👁️ Section 2: The Hidden Culprit – Windows Hello
To fully grasp why your Remote Desktop login attempt fails—even when your credentials seem accurate—you must first understand what Windows Hello actually is and how it works beneath the surface.
🔐 What Is Windows Hello?
Windows Hello is Microsoft’s modern authentication system introduced with Windows 10. It was designed to replace traditional passwords with biometric-based or PIN-based sign-ins, offering a faster, more secure, and more convenient experience for users. With Windows Hello, users can:
- Sign in using a PIN code
- Use facial recognition via an infrared or 3D camera
- Use a fingerprint scanner for instant access
It’s intuitive, fast, and secure. In fact, Microsoft promotes Windows Hello as a “passwordless” future—a safer alternative that doesn’t rely on passwords stored in plaintext or even in memory.
⚙️ How Windows Hello Works (Under the Hood)
Here’s where the problem begins. When you use Windows Hello to sign in, your actual Windows account password is never used or cached in the session. Instead:
- The login process generates a cryptographic token secured by your TPM (Trusted Platform Module) chip.
- This token is locally verified—never sent across the network.
- No password hash or credential is stored that Remote Desktop Protocol (RDP) can use later.
Windows considers this a valid local sign-in, but RDP doesn’t.
Remote Desktop requires traditional credentials—specifically, a password—to generate and verify authentication hashes using protocols like NTLM or Kerberos. But if you’ve never logged in with a password (especially after a recent password change, domain policy update, or OS upgrade), then your system literally doesn’t have what RDP needs to validate you.
🧱 Why This Breaks Remote Desktop Authentication
Let’s put this into context with an example:
- You start your Windows 11 laptop and sign in with your facial recognition via Windows Hello.
- The system opens up, and everything works as expected.
- Later, you attempt to RDP into this machine from your desktop at home.
- You enter the correct username and password, and expect to log in.
- Instead, you receive a “Your credentials did not work” error.
What happened?
- Your local session never authenticated your password.
- The system never generated or cached a password-derived credential.
- RDP has no valid password-based token to use for NTLM/Kerberos authentication.
- Result: authentication fails, despite using the “right” password.
This is not a bug in RDP. This is by design—because Windows Hello was never meant to interact with RDP directly.
😓 Why It Confuses Users So Easily
This creates an unusual contradiction:
You can access your computer perfectly using Windows Hello—but you can’t access it remotely unless you sign in using your password.
For most users, this doesn’t make intuitive sense. “If I can log in locally with my face or PIN, why can’t RDP use the same logic?” The answer is: because Windows Hello is a local-only authentication mechanism, whereas RDP relies on domain/network-capable credentials.
Microsoft’s own documentation only briefly references this, and error messages during RDP login don’t point to Windows Hello at all, leaving users bewildered.
🧠 Section 3: Why Password-Based Login Works
Now that we’ve identified Windows Hello as the source of the problem, the natural next question is:
Why does switching to password-based login suddenly allow RDP to work?
The answer lies in how Windows manages authentication credentials and how those credentials interact with Remote Desktop Protocol (RDP) services under the hood.
🔑 The Role of Traditional Passwords in Windows Authentication
In Windows operating systems, when a user signs in using their actual account password, the following key things happen:
- The password is hashed and processed through authentication protocols like NTLM (NT LAN Manager) or Kerberos, depending on whether the machine is part of a domain.
- A valid session token is generated and stored in memory by the LSA (Local Security Authority) subsystem.
- This token and associated password-derived hash are available to background services, including Remote Desktop Services.
This is important because RDP relies entirely on these password-based mechanisms to authenticate remote login attempts. Unlike Windows Hello, which is validated locally with no network credential generation, password login creates session credentials that are reusable across services—including those accessed over the network.
🔄 How Switching to a Password Fixes the Issue
Let’s walk through the chain of events when you switch from a Hello-based login to a password-based login:
- You sign out of your session (which may have been authenticated with a PIN or biometrics).
- You sign in again, this time explicitly using your Windows password.
- During login, your credentials are processed through standard Windows authentication protocols.
- The system stores your session credentials in memory (LSA) in a way that can be reused by services like RDP.
- You now initiate an RDP session from another machine.
- Because your user session is now “anchored” by valid, password-derived credentials, RDP can authenticate your remote login successfully.
So essentially, the password doesn’t just let you in—it lets the system know that your identity can be shared with other services.
🧬 Why Windows Hello Can’t Do the Same
Despite its modern security design, Windows Hello is intentionally isolated from legacy authentication mechanisms like NTLM. It’s a local trust system, meaning:
- It proves you are you to your local machine.
- It does not prove anything to remote services or networks.
- It does not generate NTLM hashes or Kerberos tickets.
That means even if you know your password, as long as you don’t actually log in with it, Windows won’t cache it—and RDP won’t be able to use it.
💡 Real-World Analogy
Imagine you enter a secure office building using facial recognition. You pass through security, go to your desk, and start your workday.
Later, your manager needs to verify your identity in the HR system—but that system only accepts your ID badge number, which you never used today. As far as the HR system is concerned, you were never officially registered as “present” because you bypassed the ID scanner.
Your face got you in—but the system that matters was left out of the loop.
That’s what happens when you use Windows Hello for local access and then try RDP.
✅ Summary of This Section:
| Authentication Method | Valid for RDP? | Why |
|---|---|---|
| Windows Hello (PIN, Face ID) | ❌ No | Local-only, no password hash generated |
| Password-based login | ✅ Yes | Generates reusable credentials for RDP |
🛠️ Section 4: Step-by-Step Fix — Logging In with Your Password to Enable RDP Access
Now that you understand why RDP login fails when Windows Hello is used and why password-based login is required, it’s time to take action. The fix is straightforward, effective, and requires no registry hacks or group policy changes—just a simple switch in how you sign into your PC.
Here’s how to resolve the problem, step by step.
🔁 Step 1: Sign Out of the Current Windows Hello Session
If you’re currently signed in with Windows Hello—whether via PIN, fingerprint, or facial recognition—you’ll first need to sign out of your account to reset the session context.
How to do it:
- Press
Ctrl + Alt + Deleteon your keyboard. - Click “Sign out”.
- Wait until you’re back at the Windows sign-in screen.
💡 Important: Simply locking your computer (
Win + L) is not enough. You must fully sign out to clear the cached Hello-only session.
🔑 Step 2: Log In Using Your Account Password (Not a PIN or Face)
Now, from the Windows login screen, you’ll deliberately avoid using Windows Hello. Instead, you’ll manually choose to log in with your actual password.
How to do it:
- On the login screen, locate and click “Sign-in options” (usually under the password field or under the profile photo).
- Select the key icon, which represents traditional password login.
- Enter your full Windows account password and press Enter.
⚠️ If you don’t remember your password, you must reset it before proceeding. This method only works with correct, confirmed credentials.
Once you’ve signed in this way, your session is authenticated using your real password, which is now stored securely in the LSA (Local Security Authority). This session context is what enables successful RDP authentication.
🖥️ Step 3: Reattempt Your Remote Desktop Connection
Now that you’ve logged in correctly, you’re ready to reattempt your RDP connection from another device.
How to do it:
- Open Remote Desktop Connection (you can search for
mstscin the Start Menu). - Enter the IP address or hostname of the target machine.
- Provide the same username and password you just used for local login.
- Press Connect.
✅ This time, you should be logged in successfully without errors like “Your credentials did not work.”
💬 If you’re using saved credentials or a
.rdpfile, delete and re-enter your credentials to ensure they are synced with the new session.
🧪 Step 4 (Optional): Verify RDP-Related Settings
Though not always necessary, if you’re still having issues, confirm the following settings on the target machine:
- RDP is enabled:
Settings > System > Remote Desktop > Enable Remote Desktop - The user is allowed to connect via RDP:
Go toSystem Properties > Remote> Under “Remote Desktop,” click “Select Users…” and ensure your account is listed. - The firewall is open for RDP (TCP port 3389):
Runwf.msc> Check inbound rules for “Remote Desktop – User Mode.”
💬 Step 5: Future Prevention Tips
- Always use password login at least once after changing your Windows password, even if you prefer Windows Hello day-to-day.
- If you frequently use RDP, consider disabling Windows Hello on the target machine to avoid session mismatch.
- For enterprise users, use Group Policy or Intune to enforce password-based login for RDP endpoints.
✅ Quick Recap of the Fix
| Step | Action |
|---|---|
| 1 | Sign out of your current Hello-based session |
| 2 | Sign in using your Windows password |
| 3 | Retry RDP connection with the same credentials |
| 4 (Optional) | Double-check RDP, firewall, and user access settings |
⚙️ Section 5: Advanced Technical Note – Why RDP Needs Password-Based Authentication
At this point, you know that signing in with your Windows password—rather than using Windows Hello—is the key to fixing Remote Desktop login issues. But if you’re a power user, system administrator, or just someone who likes to understand why things work the way they do, this section is for you.
Let’s dive into the underlying authentication mechanisms that determine why Remote Desktop Protocol (RDP) fails without a password-based session—and why password login enables successful authentication.
🔐 Windows Authentication Mechanisms: NTLM and Kerberos
When you connect to a Windows machine via RDP, the authentication process depends on either:
- NTLM (NT LAN Manager) – common in workgroup or local account environments
- Kerberos – preferred in domain-based environments (e.g., Active Directory)
Both authentication protocols rely on the presence of a password hash to validate a user’s identity. Specifically:
- NTLM uses an encrypted version of your password to challenge and verify your identity.
- Kerberos uses a “ticket-granting” model, which still requires your password-derived credentials to issue service tickets.
📌 Key takeaway: Neither NTLM nor Kerberos can authenticate a user based on a PIN, facial recognition, or fingerprint data alone.
🔎 Why Windows Hello Breaks This Flow
Windows Hello intentionally bypasses the use of your plaintext password or its derived hash. Here’s what happens instead:
- When you sign in using Windows Hello, the system uses asymmetric key pairs stored in a secure TPM (Trusted Platform Module) on your device.
- These keys authenticate your identity locally using public/private key cryptography.
- No password or reusable hash is created during the session.
That means no NTLM hash, no Kerberos ticket, and no way for RDP to authenticate your session remotely.
Even if you try to connect via RDP using your actual password, it may still fail if the session was initiated using Hello, because the system lacks a valid context to perform the remote handshake.
🧠 The Role of the LSA (Local Security Authority)
When you sign in using your actual password, Windows securely caches your authentication information inside the Local Security Authority Subsystem (LSASS), also known as LSA.
- This cache includes your login session token.
- It holds your password-derived credentials.
- These are accessible to authenticated system services—like Remote Desktop Services.
Remote Desktop queries LSA to validate whether it can impersonate the user’s credentials and allow access.
👉 If you used Windows Hello instead, this cache doesn’t contain valid credentials, and RDP authentication fails.
🧬 Why This Is By Design (Not a Bug)
It’s important to understand that this isn’t a flaw or oversight in Windows. It’s a security feature by design. Windows Hello is meant to:
- Increase security by avoiding passwords entirely.
- Isolate login credentials from malware and remote attack vectors.
- Prevent credential reuse or unauthorized token access.
Because of this security model, Windows Hello credentials are deliberately non-portable, even within the same device—especially not to services like RDP.
🧪 RDP Needs Credential Delegation
In technical terms, RDP uses Credential Delegation to impersonate a user during session initiation. This delegation requires:
- A valid password hash in memory (for NTLM), or
- A Kerberos TGT (Ticket Granting Ticket) available to the user session
These are only generated when you log in with a password. That’s why RDP only works after you’ve authenticated the session properly with a traditional password.
✅ Final Technical Summary:
| Component | Windows Hello | Password Login |
|---|---|---|
| Local Session Auth | ✅ Yes | ✅ Yes |
| RDP-Compatible Credentials | ❌ No | ✅ Yes |
| NTLM/Kerberos Ready | ❌ No | ✅ Yes |
| Stored in LSA | ❌ No | ✅ Yes |
| RDP Login Success | ❌ No | ✅ Yes |
🧭 Section 6: Final Summary and Best Practices for Reliable RDP Access
After a detailed deep dive into the RDP login issue caused by Windows Hello, it’s time to bring everything together. This section will summarize the core insights, provide practical tips for long-term prevention, and address frequently asked questions to ensure you’re never locked out of your own system again.
✅ Final Summary: The Core Truth
| Issue | RDP login fails despite using the correct credentials |
|---|---|
| Root Cause | The local session was authenticated with Windows Hello (not password) |
| Why It Matters | RDP requires NTLM/Kerberos-compatible password credentials |
| Fix | Sign out and log in again using your Windows password before attempting RDP |
The problem doesn’t lie in your network, firewall, or account configuration—it’s how you logged in locally. The solution is refreshingly simple: bypass Windows Hello and log in with your real password before using Remote Desktop.
🛡️ Best Practices to Avoid This Problem in the Future
To ensure smooth RDP access in the future, here are some proactive steps you can take:
🔹 1. Use Password Login Regularly
Even if you prefer Windows Hello for daily use, make a habit of logging in with your password after every password change or OS upgrade to refresh credential caches.
🔹 2. Disable Windows Hello (Optional)
If you primarily use RDP or manage multiple machines:
- Use
gpedit.mscto disable Windows Hello: pgsql복사편집Computer Configuration > Administrative Templates > System > Logon > Turn off Windows Hello for Business
🔹 3. Confirm RDP and User Access Settings
Double-check that:
- RDP is enabled under:
Settings > System > Remote Desktop - Your user account is in the Remote Desktop Users group
- TCP port 3389 is open in the firewall
🔹 4. Avoid Cached Credentials
When prompted, always enter credentials manually on first RDP login after a session reset—don’t rely on old saved credentials if the session was started with Windows Hello.
🔹 5. Educate Other Users
If you manage a team or office network, make sure other users understand that PIN and Face ID logins don’t work with RDP unless they’ve used a password at least once.
❓ Frequently Asked Questions (FAQ)
Q1: Can I use RDP with a Microsoft account instead of a local account?
A: Yes, but be sure to enter the full Microsoft email address and password. Windows Hello login won’t work remotely.
Q2: Can I enable RDP access from a session logged in with PIN or fingerprint if I already know my password?
A: No. You must log in with the password to generate the credentials that RDP can use.
Q3: Does this issue affect domain-joined PCs as well?
A: Yes. While domain environments use Kerberos instead of NTLM, the requirement for password-based authentication still applies.
Q4: Are there third-party tools that bypass this issue?
A: No legitimate tool bypasses Windows credential handling securely. The correct approach is to use supported authentication methods.
Q5: Will switching to a different remote access tool like TeamViewer avoid this?
A: Yes, third-party tools have their own authentication systems and do not rely on NTLM/Kerberos—but they come with trade-offs in speed, security, and control.
Q6: What if I forgot my password and can only sign in with a PIN?
A: You must reset your password from the login screen or through account recovery before RDP will work.
🔚 Closing Thoughts
This issue is a great example of how convenience and security features—like Windows Hello—can unintentionally clash with legacy but essential tools like RDP. Understanding the distinction between local authentication and network authentication is crucial in today’s hybrid working environments.
Now that you’ve mastered the cause and fix of this frustrating RDP login problem, you’re far better equipped to maintain reliable remote access—whether you’re managing your own system or supporting a team.
🔗 Official Microsoft Documentation for Further Reading
1. Remote Desktop Services Overview (Official RDP Guide)
- 📎 URL:
https://learn.microsoft.com/en-us/windows-server/remote/remote-desktop-services/welcome-to-rds - 📘 Description:
This is Microsoft’s official introduction to Remote Desktop Services (RDS). It explains how RDP works, how to configure it, and which components are involved.
2. Windows Hello for Business: Identity Verification
- 📎 URL:
https://learn.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-identity-verification - 📘 Description:
This guide explains how Windows Hello authentication works using TPM and asymmetric key pairs. It also outlines the limitations of Hello when used in enterprise or remote environments.
3. Troubleshoot Remote Desktop Client Connection Issues
- 📎 URL:
https://learn.microsoft.com/en-us/windows-server/remote/remote-desktop-services/troubleshoot/rdp-client-connection - 📘 Description:
A troubleshooting guide for common RDP connection failures, including authentication problems, configuration issues, and network errors.